Zero-Trust Architectures in Operational Technology (OT)
Zero-Trust (ZT) is a cybersecurity paradigm that eliminates implicit trust in any user, device, or network segment. The core mantra is “never trust, always verify”. In traditional IT, perimeter defenses (e.g., firewalls) assume everything inside is safe. Zero-Trust assumes breach—treating internal and external traffic equally suspiciously—and requires continuous verification for every access request.

In Operational Technology (OT) environments—like industrial control systems (ICS), SCADA, mining operations, aluminum smelting, or manufacturing—ZT is adapted carefully. OT prioritizes availability, safety, and reliability over pure confidentiality, as disruptions can cause physical harm, production halts, or safety risks. Legacy systems (often 20-30+ years old) lack modern security features, making full ZT challenging but essential amid rising threats (e.g., ransomware targeting critical infrastructure).
Core Principles of Zero-Trust in OT (Adapted from NIST SP 800-207, DoD 2025 Guidance, ISA/IEC 62443)
- Verify Explicitly: Authenticate and authorize every request based on identity, device health, context (e.g., location, time), and risk.
- Least Privilege Access: Grant only the minimum permissions needed, often just-in-time.
- Assume Breach: Monitor continuously for anomalies; segment to limit lateral movement.
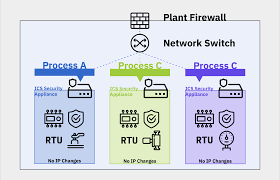
- Micro-Segmentation: Fine-grained controls beyond traditional zones (e.g., Purdue Model layers).
- Continuous Monitoring & Analytics: Log all activity; use AI/behavioral analysis for threats.
- OT-Specific Adjustments: Avoid “fail-closed” policies that could halt operations; use unidirectional data diodes for sensitive flows; prioritize non-disruptive tools.
Recent developments (as of January 2026):
- U.S. DoD released ZT guidance for OT in late 2025, defining 105 activities/outcomes (84 target-level, 21 advanced). It simplifies the Purdue Model into two layers: Process Control Layer (Levels 0-2: sensors/PLCs) and Operational Layer (Levels 3-4: SCADA/supervisory).
- Targets: Basic ZT by FY2030, advanced by FY2033.
Integration with Purdue Model for ICS/SCADA
The Purdue Enterprise Reference Architecture hierarchically segments ICS networks:
- Level 0-2: Process (sensors, PLCs, RTUs)—direct physical control.
- Level 3: Supervisory (SCADA, HMIs).
- Level 3.5: Industrial DMZ (IDMZ)—buffer zone.
- Level 4-5: Enterprise IT.
ZT overlays Purdue by applying micro-segmentation within and across levels, replacing implied trust (e.g., flat OT networks) with explicit controls. Use data diodes for one-way flows from OT to IT; enforce policy at application/workload level for legacy devices.
Implementation Challenges & Strategies in OT
- Legacy Equipment: Can’t install agents; use network-based enforcement (e.g., software-defined perimeters).
- Availability Risks: Test in “monitor-only” mode first; phased rollout.
- IT/OT Convergence: Secure remote access without VPN exposure.
- Tools: Unidirectional gateways (e.g., data diodes), SASE for remote users, OT-aware SIEM, identity-based segmentation.
| Aspect | Traditional Perimeter (Purdue Alone) | Zero-Trust OT |
|---|---|---|
| Trust Model | Implicit inside zones | None—verify every access |
| Segmentation | Macro (layer-based) | Micro (per device/flow) |
| Access | Network/location-based | Identity/context-based |
| Disruption Risk | Low initial change | Managed via phased, OT-safe deployment |
| Examples | Firewalls at IDMZ | Policy engines + diodes + continuous auth |
Benefits in Metals/Mining OT
- Protects autonomous haul trucks, AI-optimized smelters, or remote monitoring from lateral movement.
- Enables secure cloud analytics (e.g., digital twins) without exposing PLCs.
- Reduces impact from converged threats (e.g., IT ransomware spreading to OT).
Zero-Trust OT is evolutionary—not revolutionary overnight. Start with high-risk assets (e.g., SCADA interfaces), build visibility, then enforce policies. Frameworks like DoD’s 2025 guidance, NIST, and vendors (Rockwell, Dragos) provide roadmaps for safe adoption in critical sectors.
