Purdue Model Implementation Guide for OT Cybersecurity
The Purdue Enterprise Reference Architecture (PERA), or Purdue Model, provides a hierarchical framework for segmenting Industrial Control Systems (ICS) and Operational Technology (OT) networks. It ensures secure IT/OT convergence while protecting critical processes from cyber threats. Widely adopted in standards like ISA/IEC 62443, NIST SP 800-82, and Cisco/Rockwell’s Converged Plantwide Ethernet (CPwE), it emphasizes defense-in-depth, network segmentation, and the Industrial Demilitarized Zone (IDMZ/Level 3.5).
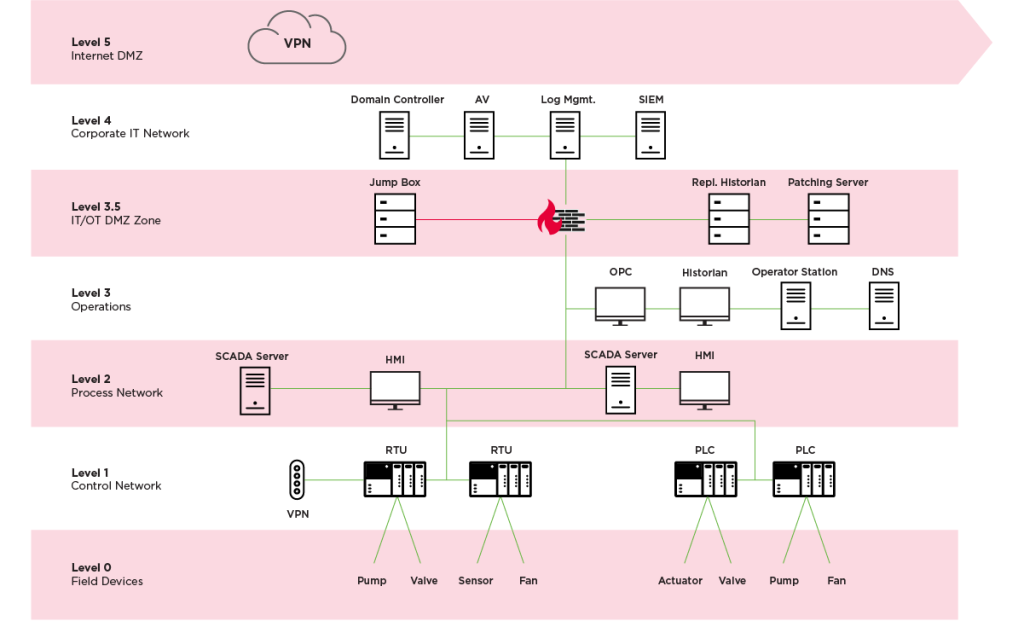
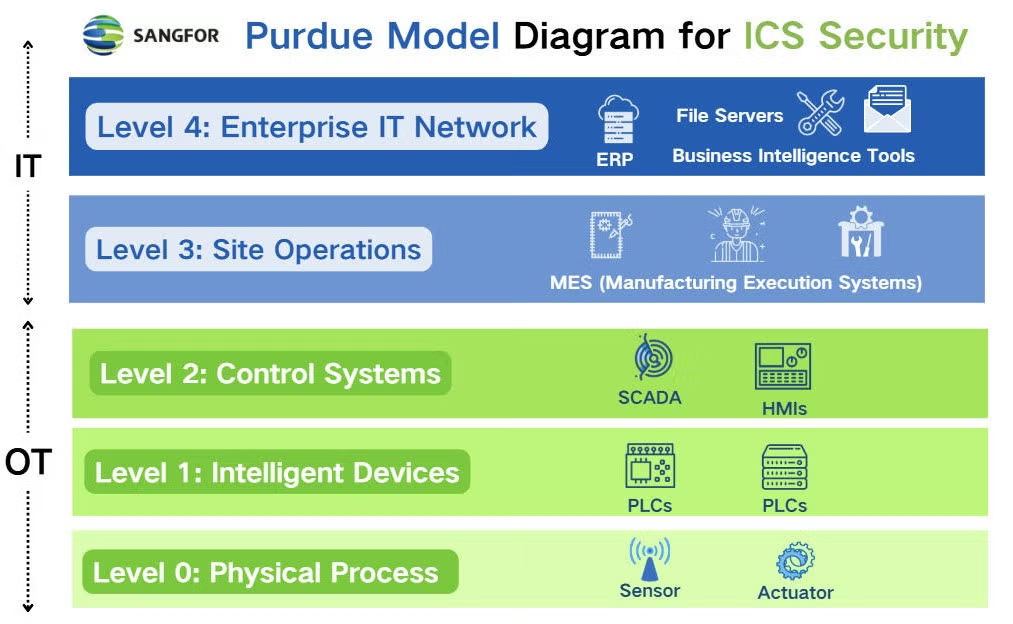
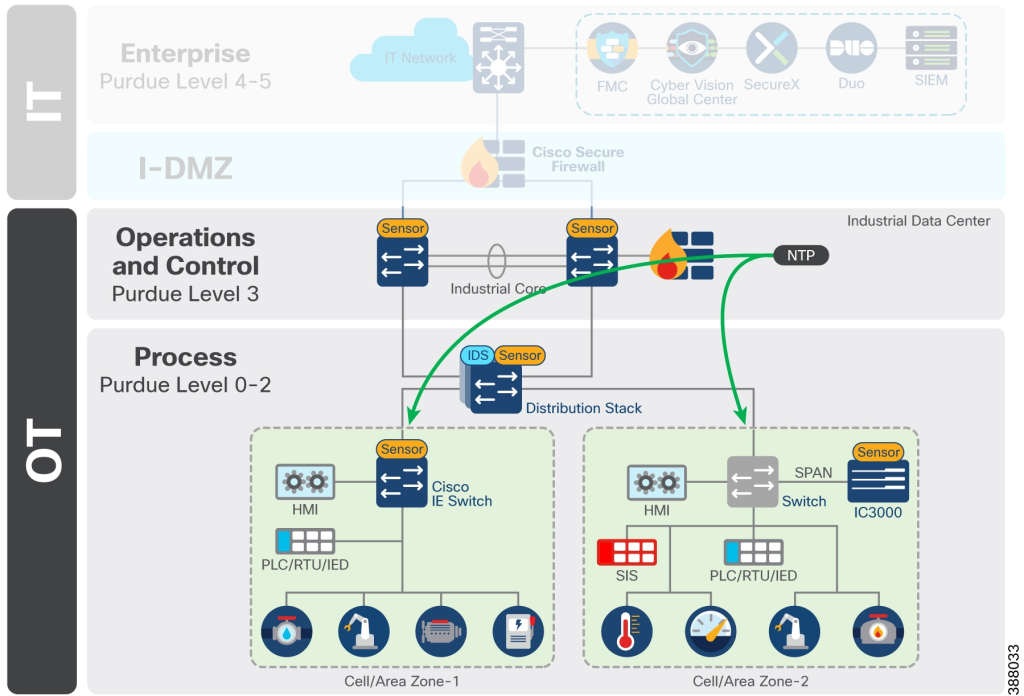
Implementation is phased to minimize disruptions in high-availability OT environments (e.g., metals/mining smelters, autonomous operations). Key resources include Cisco’s CPwE Design Guides and Palo Alto Networks’ ICS blueprints.
Step-by-Step Implementation Guide
- Assessment and Planning
- Map existing assets, data flows, and network topology to Purdue levels.
- Identify critical processes, legacy systems, and required IT/OT interactions (e.g., historian data to ERP).
- Conduct risk/gap analysis; form cross-functional IT/OT team.
- Define zones/conduits per ISA/IEC 62443 overlay.
- Asset Inventory and Visibility
- Deploy OT visibility tools (e.g., Cisco Cyber Vision, Claroty) for passive discovery.
- Catalog devices by level (PLCs at Level 1, SCADA at Level 2).
- Baseline normal traffic patterns.
- Design Logical Zones and Boundaries
- Assign assets to levels; introduce IDMZ (Level 3.5) as buffer.
- Plan macro-segmentation (IT vs. OT) first, then micro (within OT cells).
- Incorporate unidirectional flows (data diodes) for sensitive data.
- Implement Network Segmentation
- Deploy firewalls (e.g., next-gen with DPI for OT protocols) at boundaries.
- Configure restrictive rules: Deny-by-default, whitelist essential ports/protocols (e.g., Modbus, OPC UA).
- Establish IDMZ with proxies/mirrored services—no direct traversal.
- Deploy Controls and Services
- Harden devices (patching where possible, least privilege).
- Add monitoring (SIEM/SOAR), endpoint protection (OT-safe), and remote access (ZTNA).
- Overlay Zero-Trust for dynamic verification.
- Testing and Phased Rollout
- Test in monitor-mode; simulate traffic/attacks.
- Pilot one cell/site; validate no downtime.
- Gradually enforce policies.
- Ongoing Operations and Maintenance
- Continuous monitoring, anomaly detection.
- Regular audits, updates, incident response integration.
- Train staff; evolve with IIoT/cloud.
| Step | Key Actions | Tools/Best Practices | Estimated Timeline |
|---|---|---|---|
| 1. Planning | Mapping, risk assessment | Discovery tools | 1-3 months |
| 2. Visibility | Inventory baselines | Passive sensors | 1-2 months |
| 3. Design | Zones, IDMZ | CPwE guides | 1-2 months |
| 4. Segmentation | Firewalls, rules | DPI, data diodes | 2-6 months |
| 5. Controls | Hardening, ZT | PAM, UEBA | Ongoing |
| 6. Testing | Simulations | Pen tests | 1-3 months |
| 7. Maintenance | Monitoring | SOC integration | Continuous |
Benefits and Challenges
- Benefits: Contains breaches (e.g., prevents IT ransomware OT spread), enables secure analytics, supports compliance.
- Challenges: Legacy flat networks, downtime risks—mitigate with phased approach and OT expertise.
For detailed validated designs, refer to Cisco/Rockwell CPwE guides. This framework is essential for Mining 4.0 resilience amid rising threats.
