SCADA Network Segmentation Details
Supervisory Control and Data Acquisition (SCADA) systems monitor and control industrial processes in critical infrastructure (e.g., power grids, water treatment, manufacturing, metals/mining). Segmentation isolates SCADA components to limit lateral movement during cyberattacks, prevent IT threats from reaching OT, and ensure availability/safety. It forms a core defense-in-depth strategy, aligned with frameworks like the Purdue Enterprise Reference Architecture (PERA/Purdue Model), ISA/IEC 62443, and NIST SP 800-82.
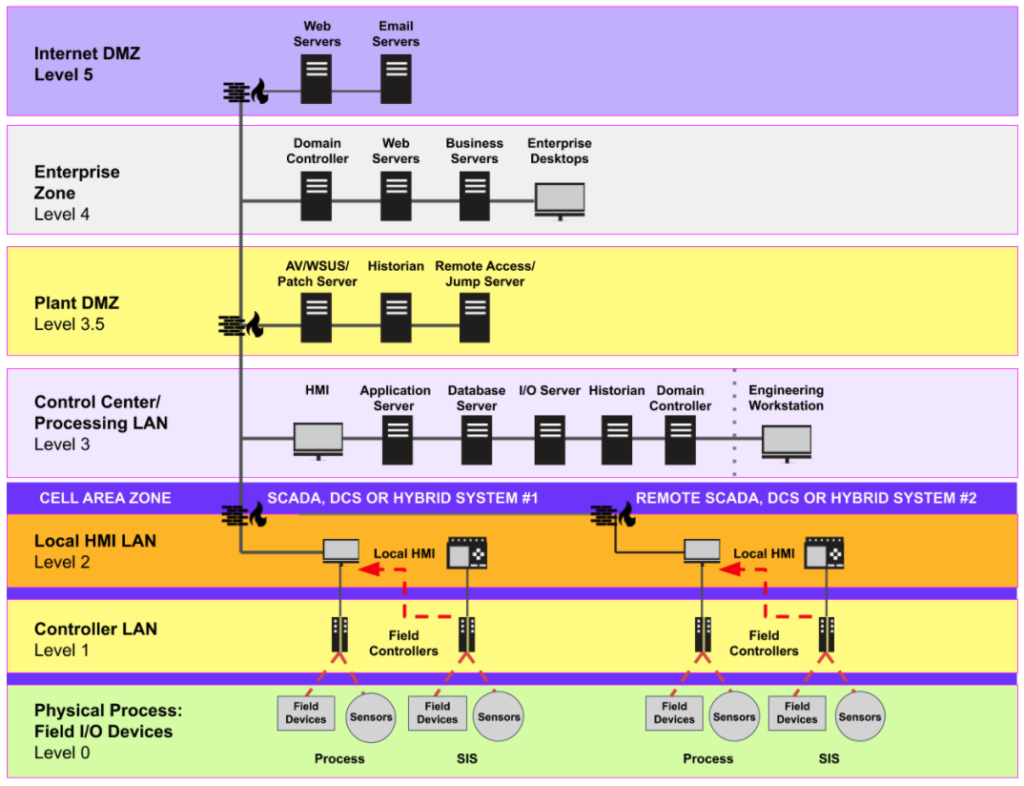
1. Purdue Model: Hierarchical Segmentation
The Purdue Model divides ICS/SCADA networks into levels based on function and response time, enforcing segmentation via firewalls, VLANs, or access controls between layers.
| Level | Description | Typical Components | Segmentation Focus |
|---|---|---|---|
| 0-1 | Physical Process | Sensors, actuators, basic controls | Isolate from higher levels; often air-gapped or unidirectional flows. |
| 2 | Supervisory Control | SCADA systems, HMIs, alarm systems | Core SCADA zone; restrict inbound/outbound traffic. |
| 3 | Operations/Management | Historians, MES, patch servers | Site-level ops; firewall to Level 2. |
| 3.5 | Industrial DMZ (IDMZ) | Proxy servers, replication services | Buffer zone; no direct IT-to-OT traffic. |
| 4-5 | Enterprise/IT | Business systems, email, ERP | Separate from OT; data flows only via IDMZ. |
- Key Rule: Traffic flows upward (e.g., data from SCADA to historians), but control flows downward are strictly limited.
- IDMZ (Level 3.5): Critical buffer preventing direct IT-OT connections. All cross-traffic terminates here (e.g., mirrored historians, proxy servers). Firewalls on both sides enforce “no direct paths.”
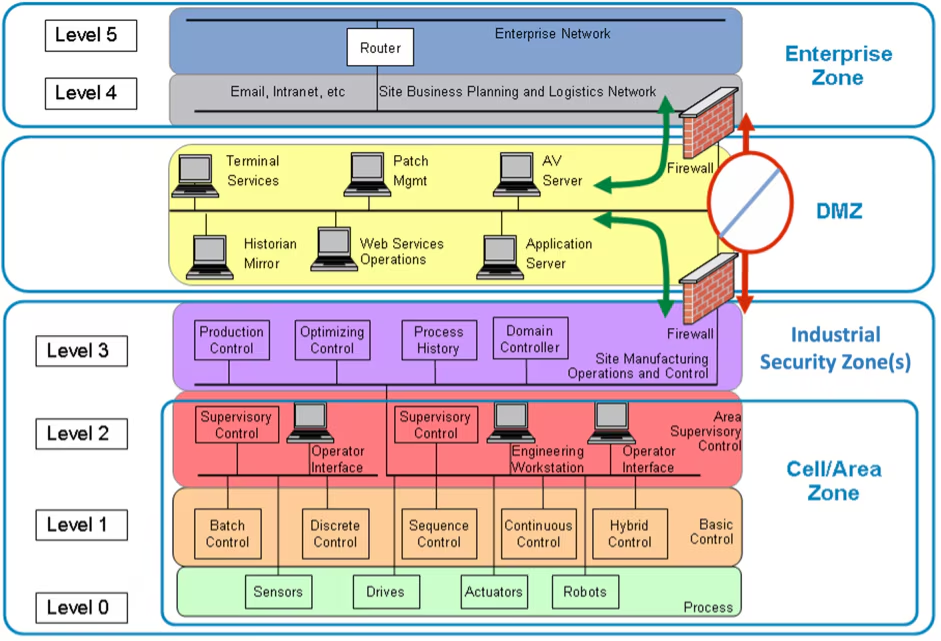
2. ISA/IEC 62443: Zones and Conduits
IEC 62443 shifts from rigid hierarchy to flexible Zones (logical/physical groupings with similar security needs) and Conduits (secure communication paths between zones).
- Zones: E.g., SCADA Zone (Level 2 assets), Cell/Area Zones (PLCs/sensors), Enterprise Zone.
- Conduits: Firewalled/VPN-protected channels with whitelisting (allow only necessary protocols/ports, e.g., Modbus from PLC to SCADA).
- Best Practice: Define conduits with unidirectional data diodes for historian uploads; use deep packet inspection for industrial protocols.
3. Macro vs. Micro-Segmentation in SCADA/OT
- Macro-Segmentation: Coarse (e.g., IT vs. OT via IDMZ; Purdue levels via firewalls). Essential baseline.
- Micro-Segmentation: Granular (per-device or flow, e.g., specific PLC only talks to its HMI). Supports Zero-Trust OT—verify every access, deny by default.
- Tools: Next-gen firewalls, NAC (e.g., Cisco ISE), software-defined perimeters.
- Benefits: Limits blast radius; enables safe IT/OT convergence.
Implementation Best Practices (2025-2026 Trends)
- Start with Visibility: Inventory assets/protocols (e.g., using OT-specific tools like Dragos or Claroty).
- Phased Rollout: Macro first (IDMZ + level boundaries), then micro (cell-level).
- Controls: Whitelist rules; unidirectional gateways for critical flows; OT-aware IDS/IPS.
- Zero-Trust Integration: Continuous verification; least privilege (e.g., just-in-time access for engineers).
- Challenges: Legacy SCADA lacks agents; prioritize non-disruptive (monitor-mode start).
- Outcomes: Reduces ransomware spread (e.g., NotPetya lessons); supports compliance (NERC CIP, IEC 62443 SL targets).
Segmentation transforms flat, vulnerable SCADA networks into resilient, zoned architectures—essential for Mining 4.0 and critical minerals ops amid rising threats.
