

Industrial Demilitarized Zone (IDMZ) Implementation Steps
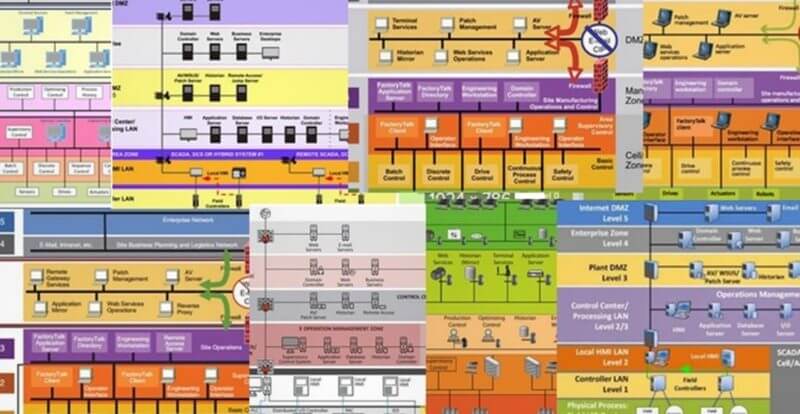
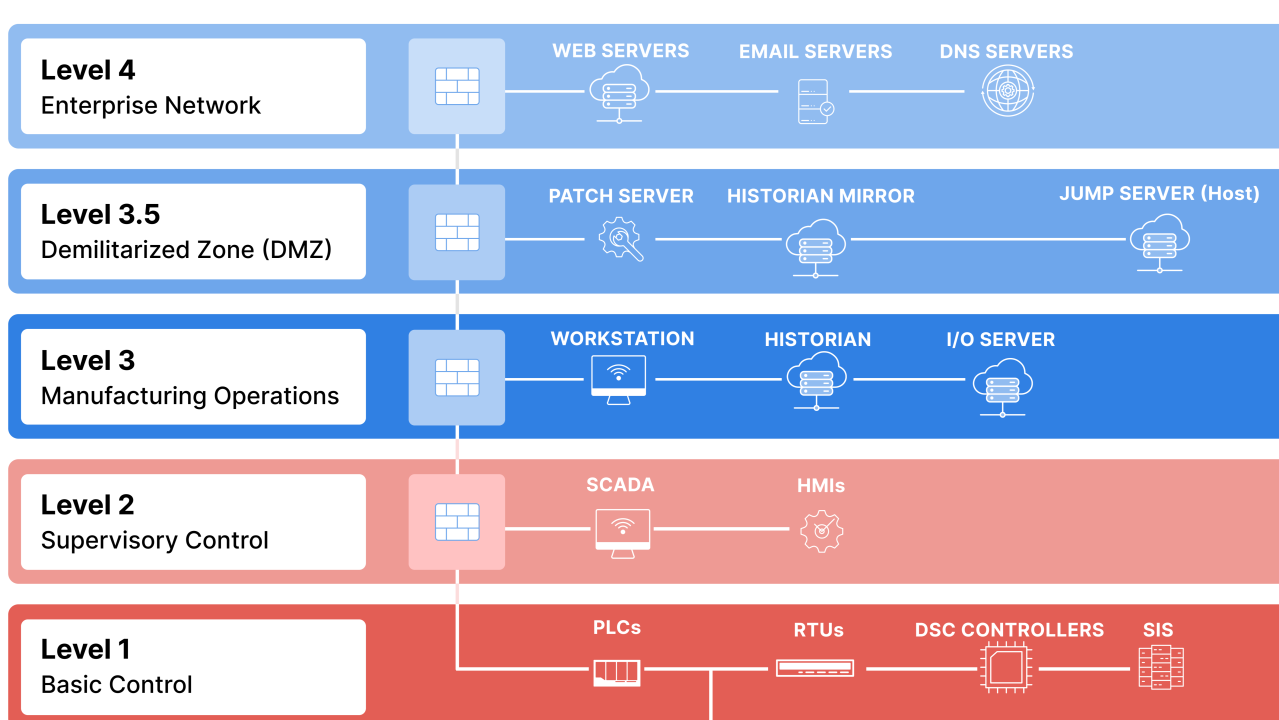
The Industrial Demilitarized Zone (IDMZ), often called Level 3.5 in the Purdue Model, is a secure buffer network between the Industrial Zone (OT – Levels 0-3) and the Enterprise Zone (IT – Levels 4-5). It prevents direct traffic between IT and OT, terminating all sessions in the IDMZ to block lateral movement of threats (e.g., ransomware from IT spilling into SCADA/PLCs). This is a core best practice in standards like ISA/IEC 62443, NIST SP 800-82, and CPwE (Cisco/Panduit/Rockwell).
Implementation follows a phased, risk-based approach to minimize disruptions in OT environments. Below are the standard steps, drawn from guides by Palo Alto Networks, Cisco, Tripwire, and others.
Step-by-Step Implementation
- Planning and Assessment
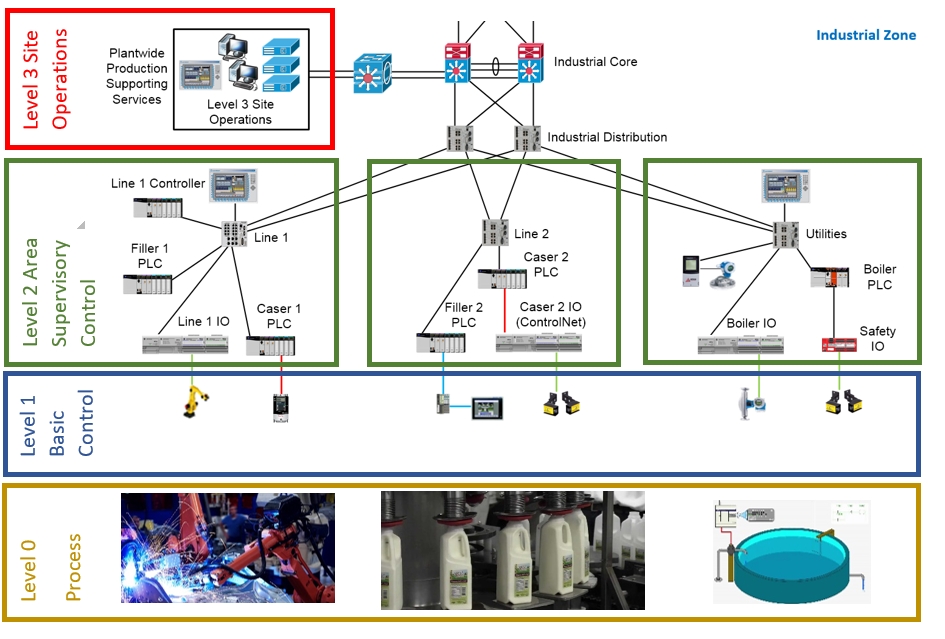
- Map current network topology, data flows, and assets across Purdue levels.
- Identify required cross-zone services (e.g., historian data to ERP, patch downloads, remote access).
- Conduct risk assessment and gap analysis (e.g., existing flat networks).
- Form a cross-functional team (IT, OT, security engineers).
- Define policies: No direct IT-OT connections; all traffic terminates in IDMZ.
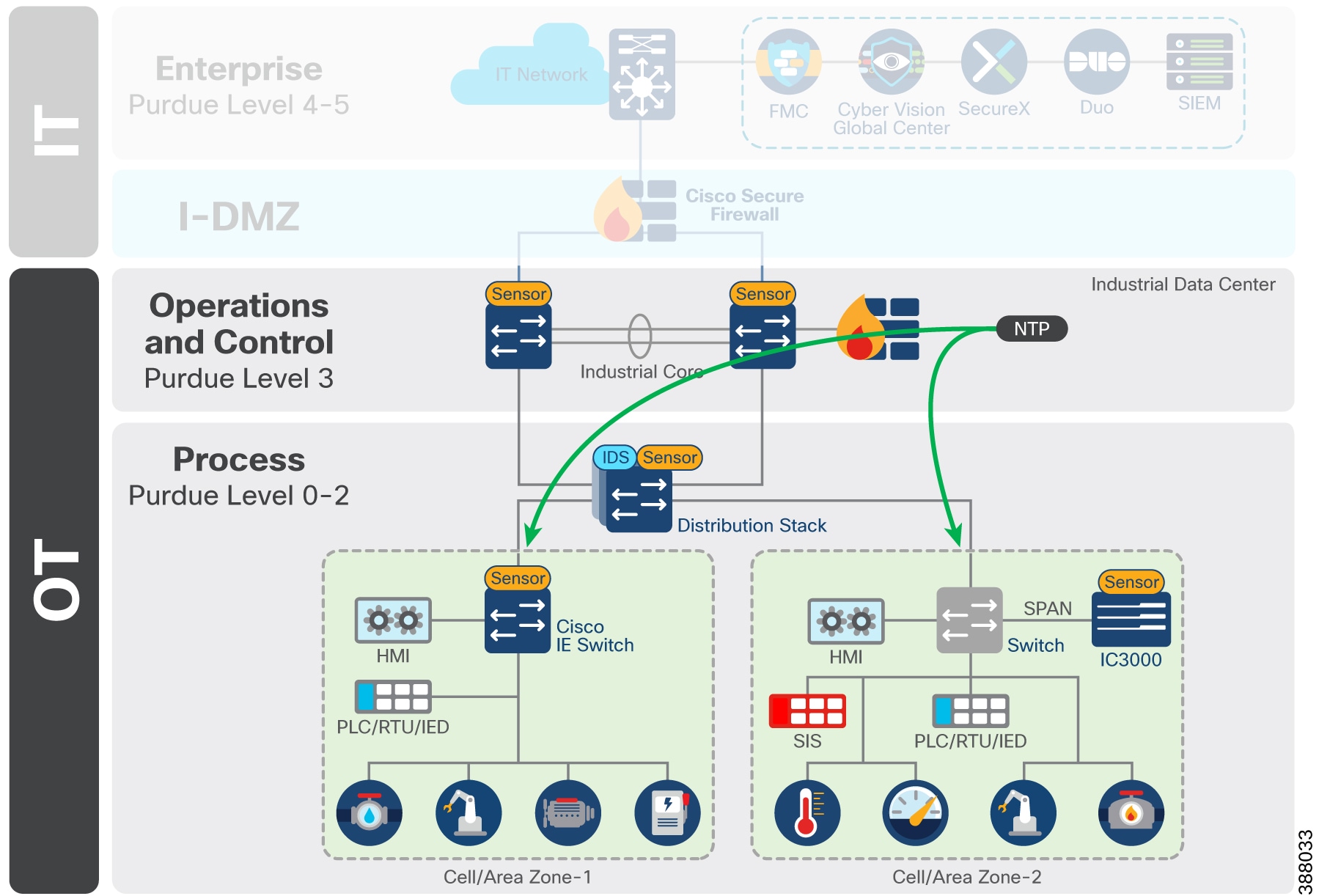
- Design the IDMZ Architecture
- Create a separate subnet/VLAN for the IDMZ.
- Deploy dual firewalls (one facing IT, one facing OT) or a single advanced firewall with zoned interfaces.
- Plan services in IDMZ: Proxy servers (e.g., reverse/web proxy for data push), mirrored historians, RDP/SSH jump hosts, antivirus/patch proxies, broker servers.
- Use unidirectional data flow where possible (e.g., data diodes for OT → IDMZ uploads; pub-sub models like MQTT).
- Deploy Network Infrastructure
- Install and harden firewalls (e.g., Palo Alto, Cisco Firepower) with stateful inspection, deep packet inspection (DPI) for industrial protocols.
- Configure restrictive rules: Deny by default; whitelist only necessary ports/protocols (e.g., OPC UA, Modbus via proxies).
- Segment with VLANs or SDN if needed.
- Implement monitoring (e.g., OT-aware SIEM logging from IDMZ).
- Place and Secure Services in IDMZ
- Deploy broker/proxy services (e.g., historian mirror that pulls from OT and pushes to IT).
- Harden servers: Patch management, antivirus, application whitelisting, and least-privilege access.
- No production OT assets (e.g., PLCs, HMIs) in IDMZ—only intermediaries.
- Migrate Data Flows and Applications
- Redirect existing flows to terminate in IDMZ (e.g., change endpoints to proxies).
- Test in stages: Monitor-only mode → phased cutover.
- Handle reverse traffic (e.g., patches) via secure proxies.
- Testing and Validation
- Simulate traffic and attacks (e.g., penetration testing).
- Verify no direct IT-OT paths (e.g., traceroute tests).
- Ensure operational continuity (availability/safety first).
- Ongoing Operations and Maintenance
- Monitor logs/anomalies.
- Regular vulnerability scans, patching (coordinated to avoid downtime).
- Change management integration.
- Periodic audits/reviews.
| Step | Key Actions | Tools/Considerations |
|---|---|---|
| 1. Planning | Asset/flow mapping, team formation | Discovery tools (e.g., Claroty, Dragos) |
| 2. Design | Dual firewalls, proxy placement | Pub-sub for data (MQTT, Kafka) |
| 3. Deployment | Firewall rules, segmentation | DPI for OT protocols |
| 4. Services | Harden proxies/historians | No persistent OT data storage |
| 5. Migration | Redirect flows | Phased rollout |
| 6. Testing | Pen tests, validation | Simulate failures |
| 7. Maintenance | Monitoring, audits | Integrate with SOC |
Successful IDMZ deployment significantly reduces risks (e.g., containing Norsk Hydro-style incidents) while enabling safe IT/OT convergence for analytics/digital twins. Start small (e.g., one site) and scale. Vendors like Palo Alto and Cisco provide detailed CVDs (Converged Plantwide Ethernet Design Guides).
