


Purdue Model Segmentation Details
The Purdue Enterprise Reference Architecture (PERA), commonly known as the Purdue Model, is a hierarchical framework developed in the 1990s for computer-integrated manufacturing and widely adopted for Industrial Control Systems (ICS) and Operational Technology (OT) network segmentation. It guides secure IT/OT convergence by dividing networks into functional levels, enforcing strict boundaries to prevent threats from spreading (e.g., ransomware from IT to critical processes). Referenced in standards like ISA/IEC 62443, NIST SP 800-82, and CISA guidelines, it remains foundational in 2026 despite IIoT/Industry 4.0 evolutions.
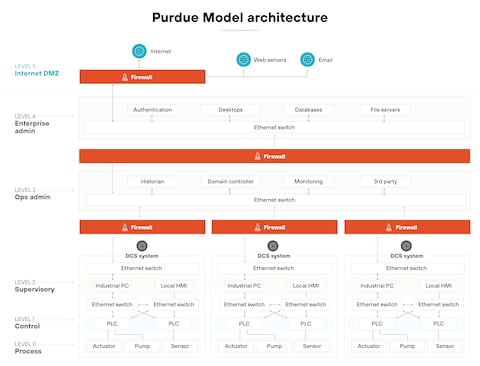
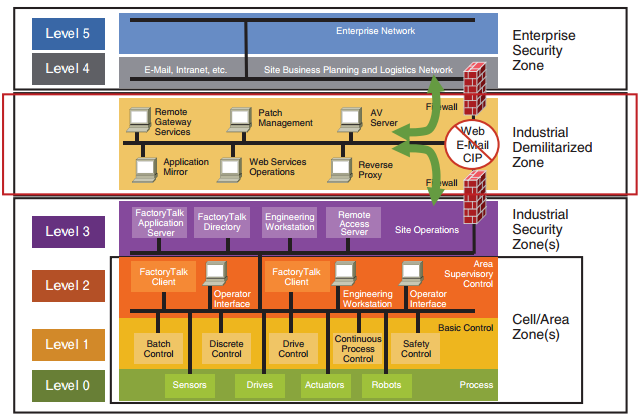
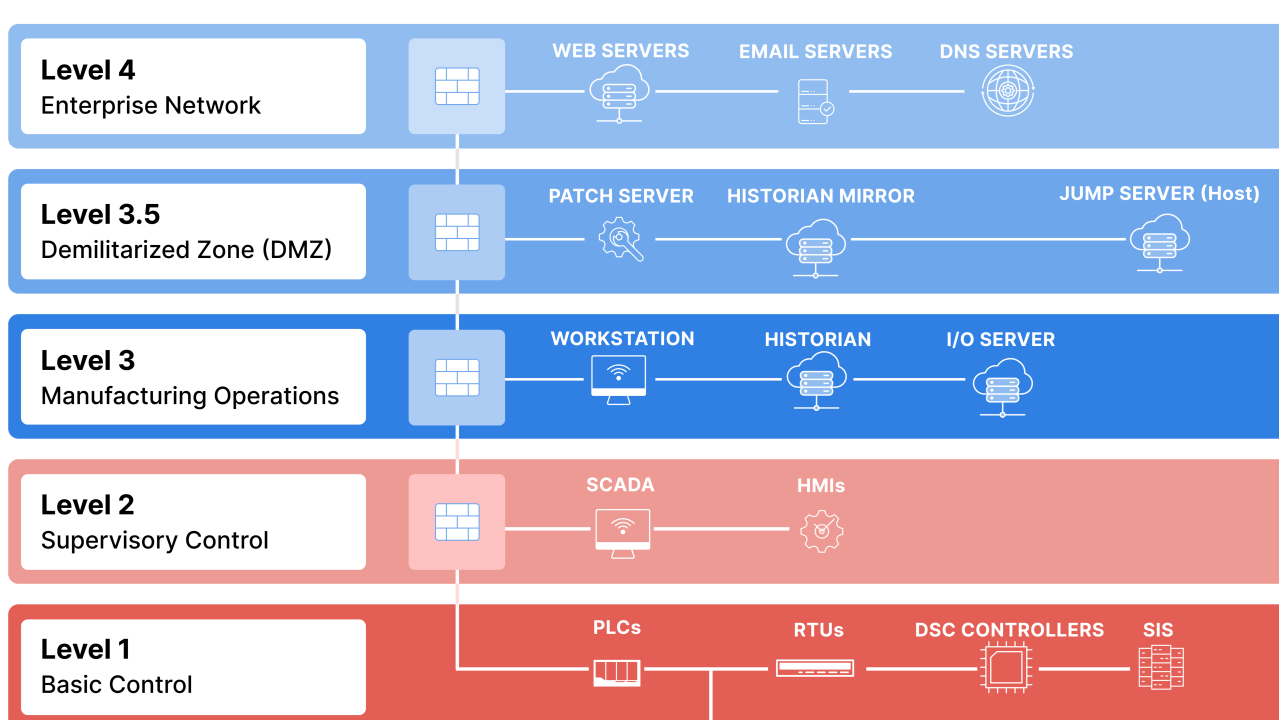
Core Levels and Segmentation Principles
The model organizes systems from physical processes to enterprise IT, with firewalls, VLANs, access controls, and unidirectional data flows between levels. Data typically flows upward (monitoring), while control flows downward are minimized/restricted.
| Level | Name | Description | Typical Components | Segmentation Controls |
|---|---|---|---|---|
| 0 | Physical Process | Sensors/actuators interacting with the environment. | Valves, motors, drives, field devices. | Air-gapped or unidirectional diodes; no direct external access. |
| 1 | Basic Control | Real-time control devices. | PLCs, RTUs, controllers. | Isolated cells; protocol whitelisting. |
| 2 | Supervisory Control | Monitoring and local control. | SCADA servers, HMIs, alarm systems. | Firewall to lower levels; restricted inbound. |
| 3 | Operations Management | Site-level functions. | Historians, MES, patch management. | Internal OT firewall; limited to Level 2 traffic. |
| 3.5 | Industrial Demilitarized Zone (IDMZ) | Buffer zone between OT and IT. | Proxy servers, mirrored historians, file shares. | Dual firewalls (no direct traversal); terminates all IT-OT sessions. |
| 4 | Business Logistics | Enterprise planning. | ERP, scheduling systems. | Enterprise firewall; read-only data from IDMZ. |
| 5 | Enterprise | Corporate functions. | Email, internet, business apps. | Fully separated; no direct OT access. |
- Key Rule: No direct traffic from IT (Levels 4-5) to core OT (Levels 0-3); all cross-boundary communication terminates in the IDMZ.
- Traffic Direction: Primarily one-way upward via data diodes or replication; downward only for approved commands.
Industrial DMZ (Level 3.5) Details
Introduced as a best practice enhancement, the IDMZ prevents direct IT-OT connections:
- Acts as a “neutral zone” with services like antivirus updates, historian mirrors, or remote access proxies.
- Enforced by firewalls on both sides: OT firewall blocks outbound except to IDMZ; IT firewall blocks inbound except responses.
- Critical for containing breaches (e.g., Norsk Hydro 2019 incident highlighted poor segmentation risks).
Modern Adaptations (2026 Context)
- IIoT/Cloud Integration: Purdue remains relevant; edge devices map to Levels 0-2, cloud to higher levels with secure conduits.
- Zero-Trust Overlay: Micro-segmentation within levels (e.g., per-PLC policies) complements macro boundaries.
- Challenges: Legacy flat networks; IIoT hyper-connectivity requires enhanced conduits/zones per IEC 62443.
The Purdue Model ensures defense-in-depth, prioritizing OT availability/safety while enabling secure data flows for Mining 4.0 analytics and digital twins. Implementation starts with visibility, then macro-segmentation (IT/OT split + IDMZ), progressing to micro.
